What 171K Real‑World Web Requests Tell Us About 2025 Browsing Habits
.webp)
With dope.security, you can create web filtering policies to Allow/Warn/Block access to specific domains on the internet. Recently, our endpoint-based secure web gateway recorded 171,000 web requests. Because enforcement happens directly on each device—our patented on-device SWG approach—we get a real-time, unfiltered view of exactly where users go and what gets blocked.
Below, we unpack the most telling patterns hiding in that data, and the business risks they expose.
1. Cloud Drives Quietly Dominate the Traffic Mix
Out of all transactions, 51,018 attempts (29.8%) targeted file-storage platforms—OneDrive, Dropbox, Box, WeTransfer, and similar. Security teams treated them seriously: 63% were blocked outright. The numbers signal how collaboration habits have changed. Forget sneaking files out over email; staff now default to a personal or shared cloud drive, often without considering data-classification rules.
“We assumed email was the main path for leaks. Turns out the real exposure lives in ‘just-share-it’ drives,” — CISO at a mid-size Healthcare company.
The primary takeaway here is that policy should focus on both what is uploaded and where it’s uploaded to, which is where an AI-powered CASB DLP that inspects content in real-time would fit perfectly with dope.security’s on-device SWG.
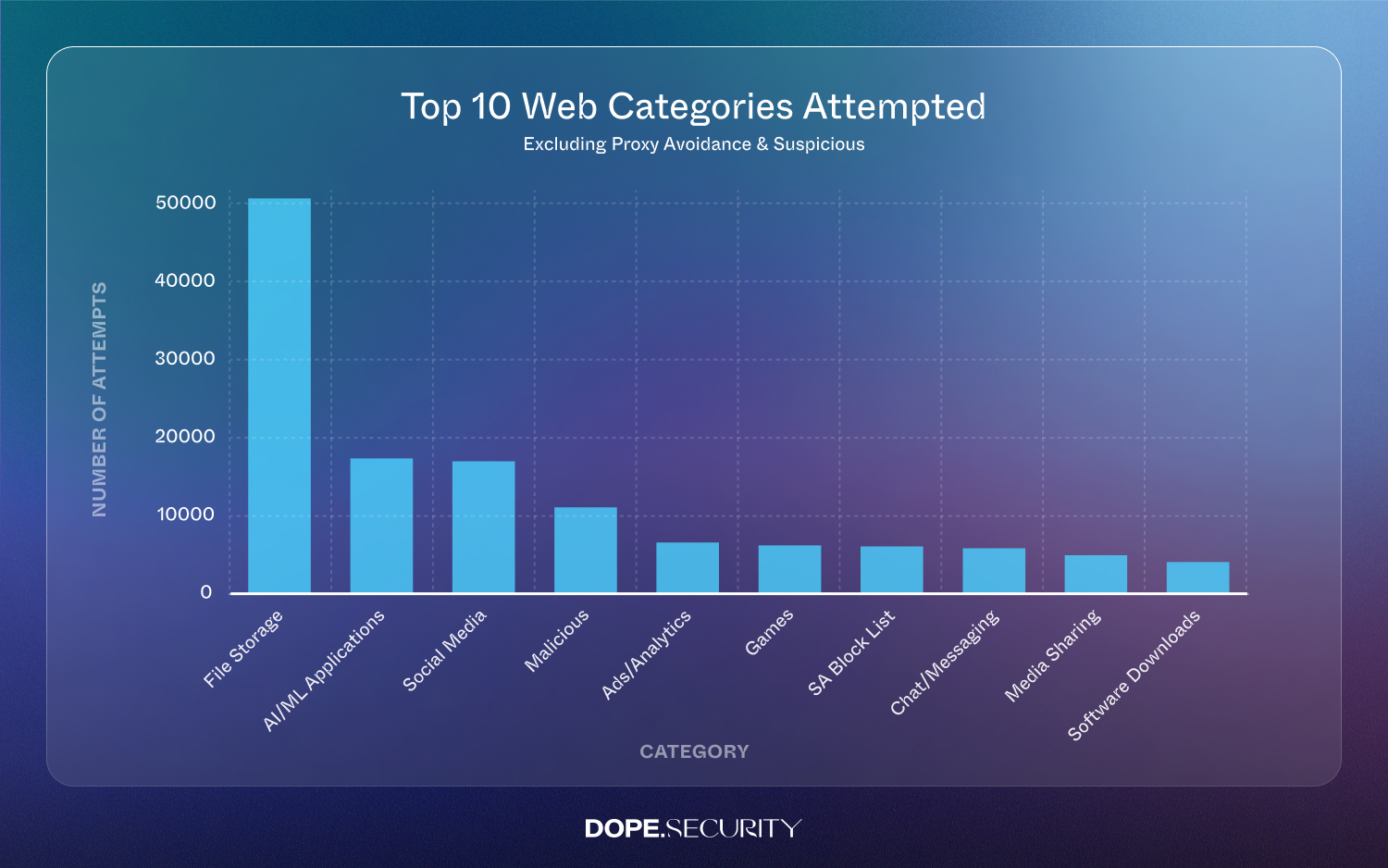
2. Generative AI Is No Longer a Side Project—It’s 10% of All Requests and Growing
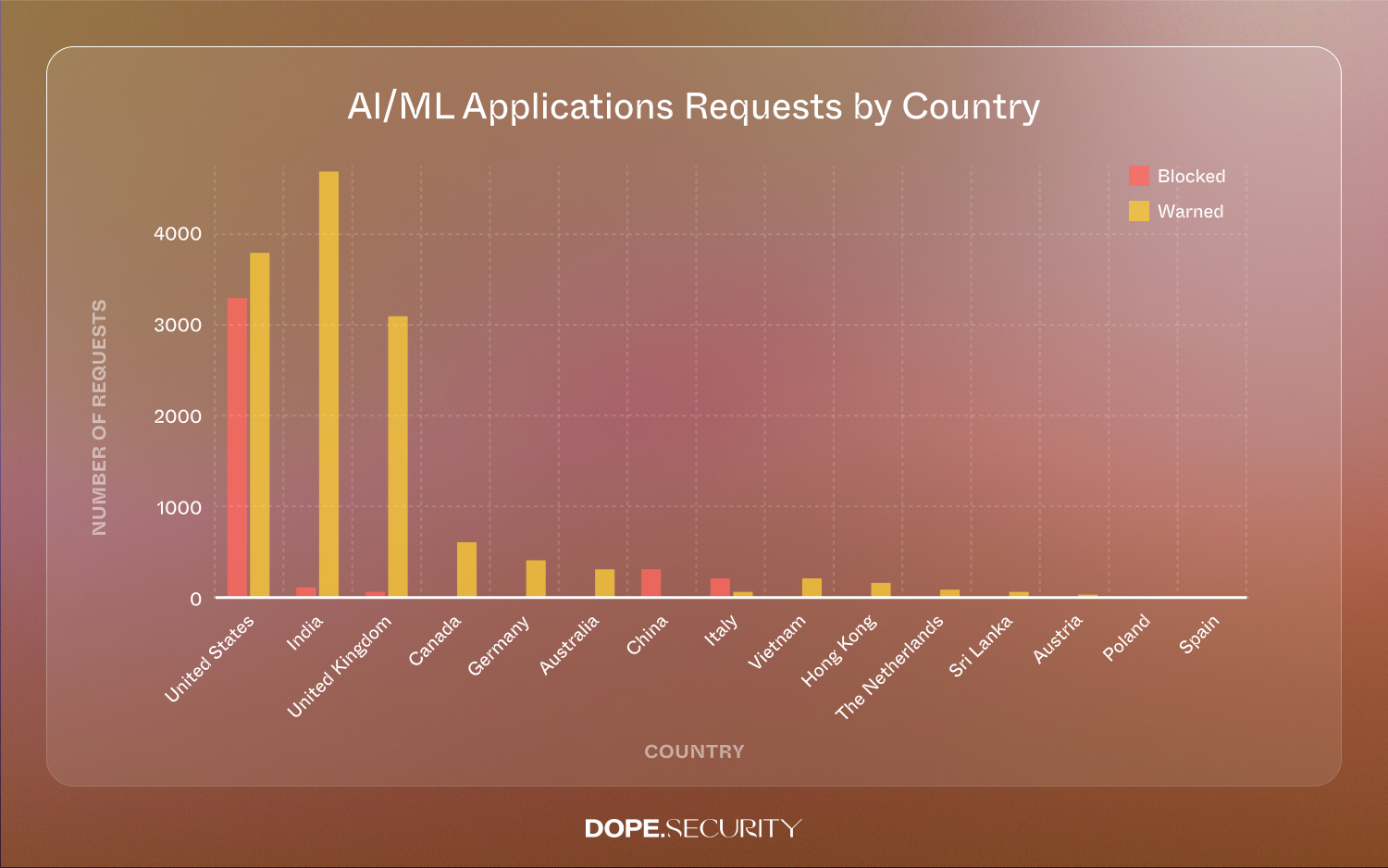
Our telemetry logged 17,129 AI/ML requests (10%), covering ChatGPT, Quillbot, Copilot extensions, and AI assistants. Interestingly, 77% generated only a warning rather than a block. That means teams are keen to encourage innovation but want to educate first.
Such spread highlights the need for flexible policy enforcement that can adapt by geography—another strength of a reliable on-device proxy that travels with the user.
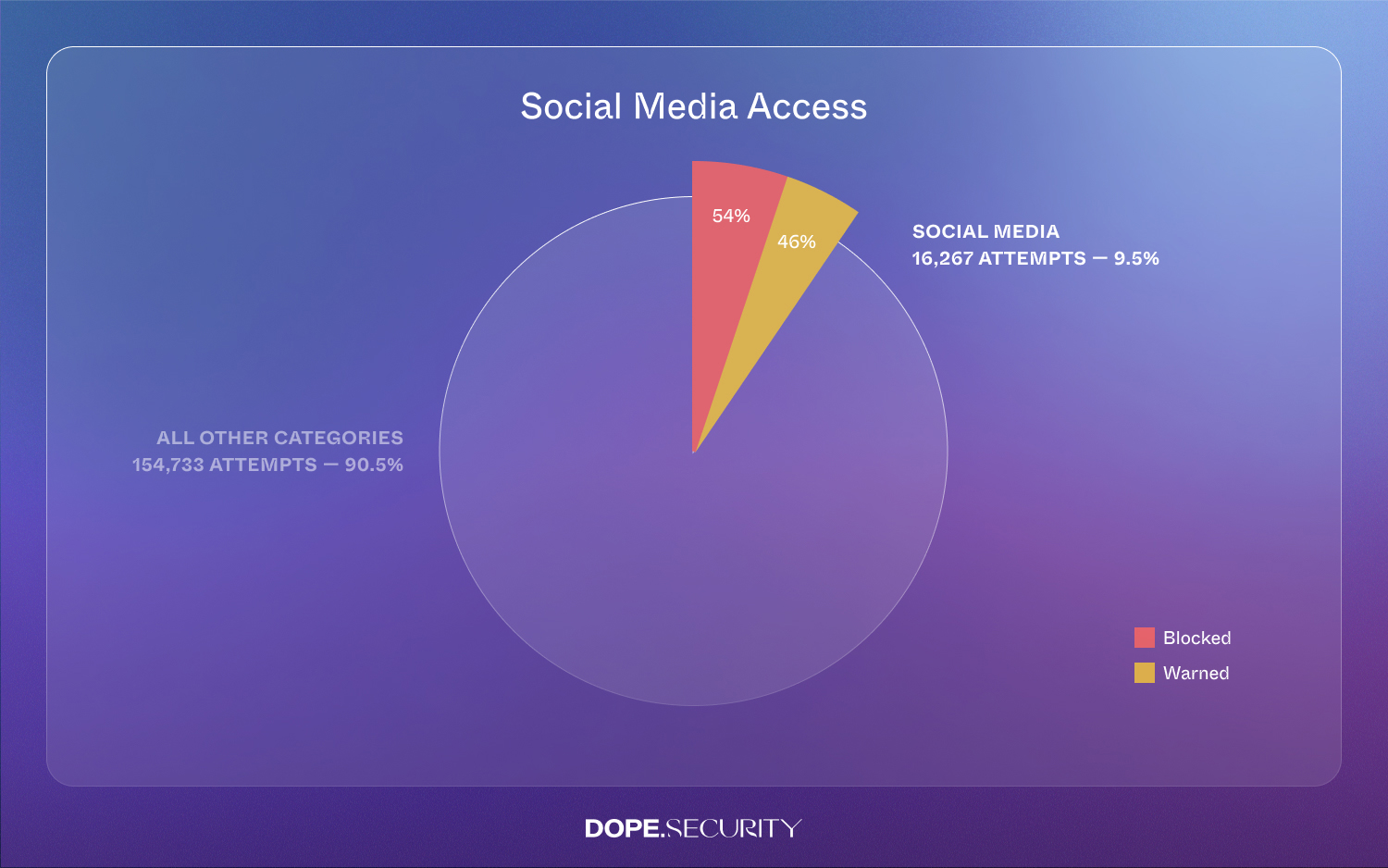
3. Social Platforms: Distraction or Brand Channel? Both.
Social Media accounted for 16,267 hits (9.5%). Teams split almost down the middle: 54% blocked, 46% warned. Marketing loves the reach; Legal worries about GDPR or brand-safety missteps. Traditional data-center proxies struggle to reconcile these competing priorities; rule updates can take hours. By contrast, an endpoint-based secure web gateway lets security push nuanced policies instantly to each device.
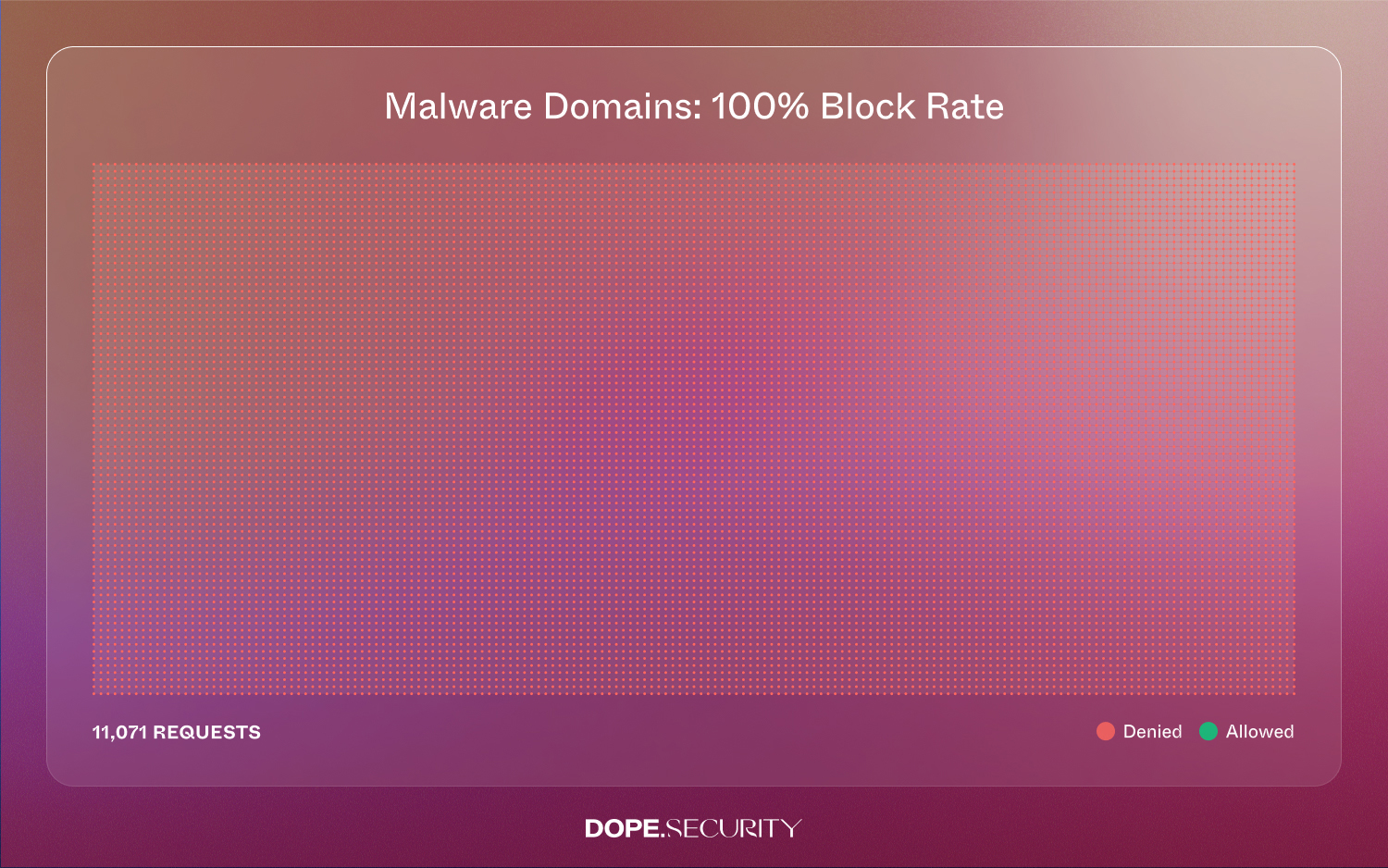
4. Malware Domains Got Zero Slack—and Zero Success
Every one of the 11,071 requests (6.5%) flagged “malicious” was denied, giving us a 100% block rate. That stat matters because many legacy stacks rely on periodic IP or DNS updates; attackers can often exploit the minutes between a reputation change and the next policy download. Local enforcement eliminates that window altogether.
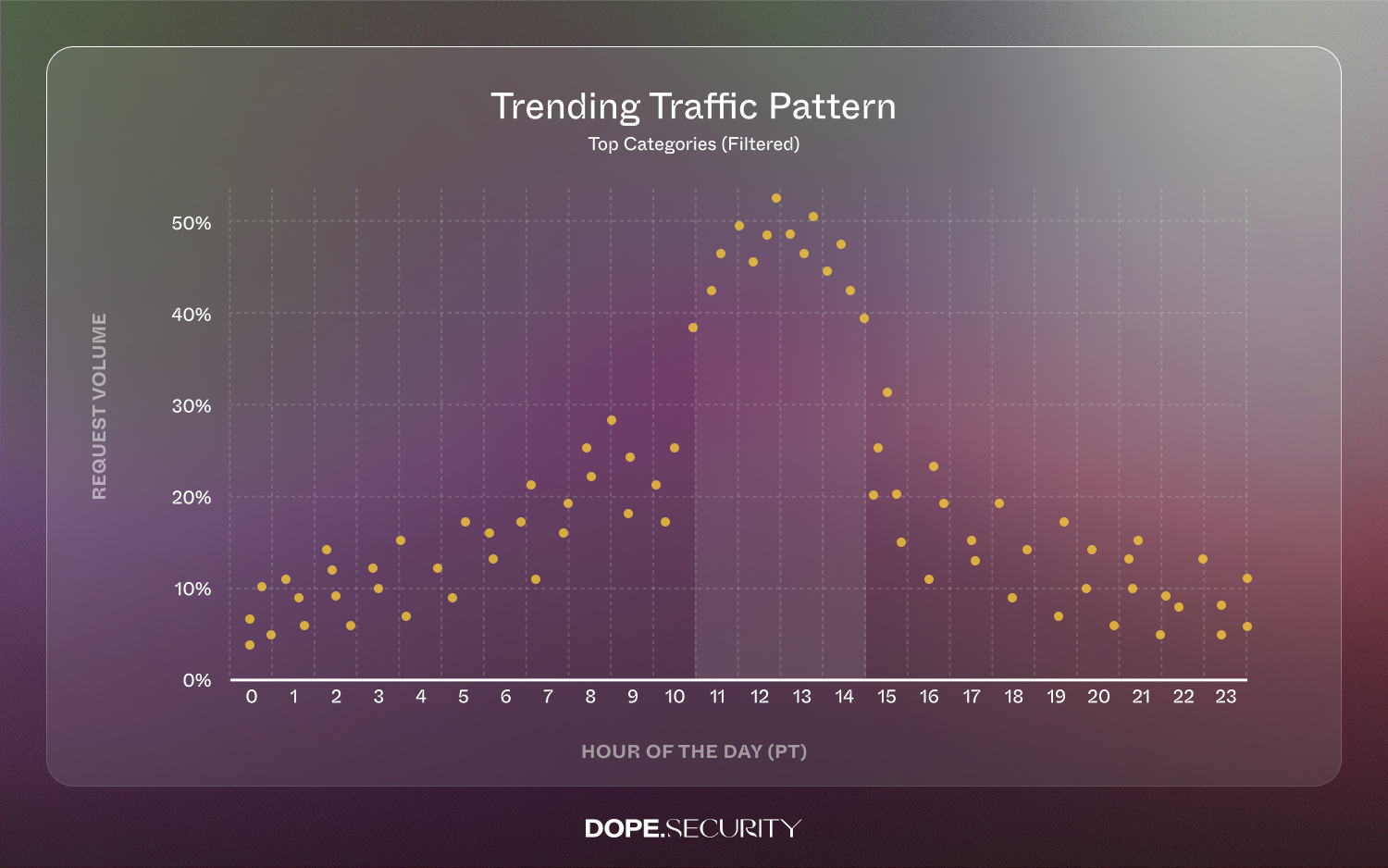
5. Lunch-Hour Spike: The Hidden Capacity Test
Plotting requests across the day shows a 40% surge between 11 AM and 2 PM Pacific Time (early afternoon for East Coast staff, end-of-day for Europe). Cloud drives, social sites, and AI tools all peak together—creating a perfect storm of risk and latency stress. Because our on-device SWG processes traffic locally, throughput is effectively uncapped. Data-center proxies, by contrast, can struggle during sudden usage bursts.
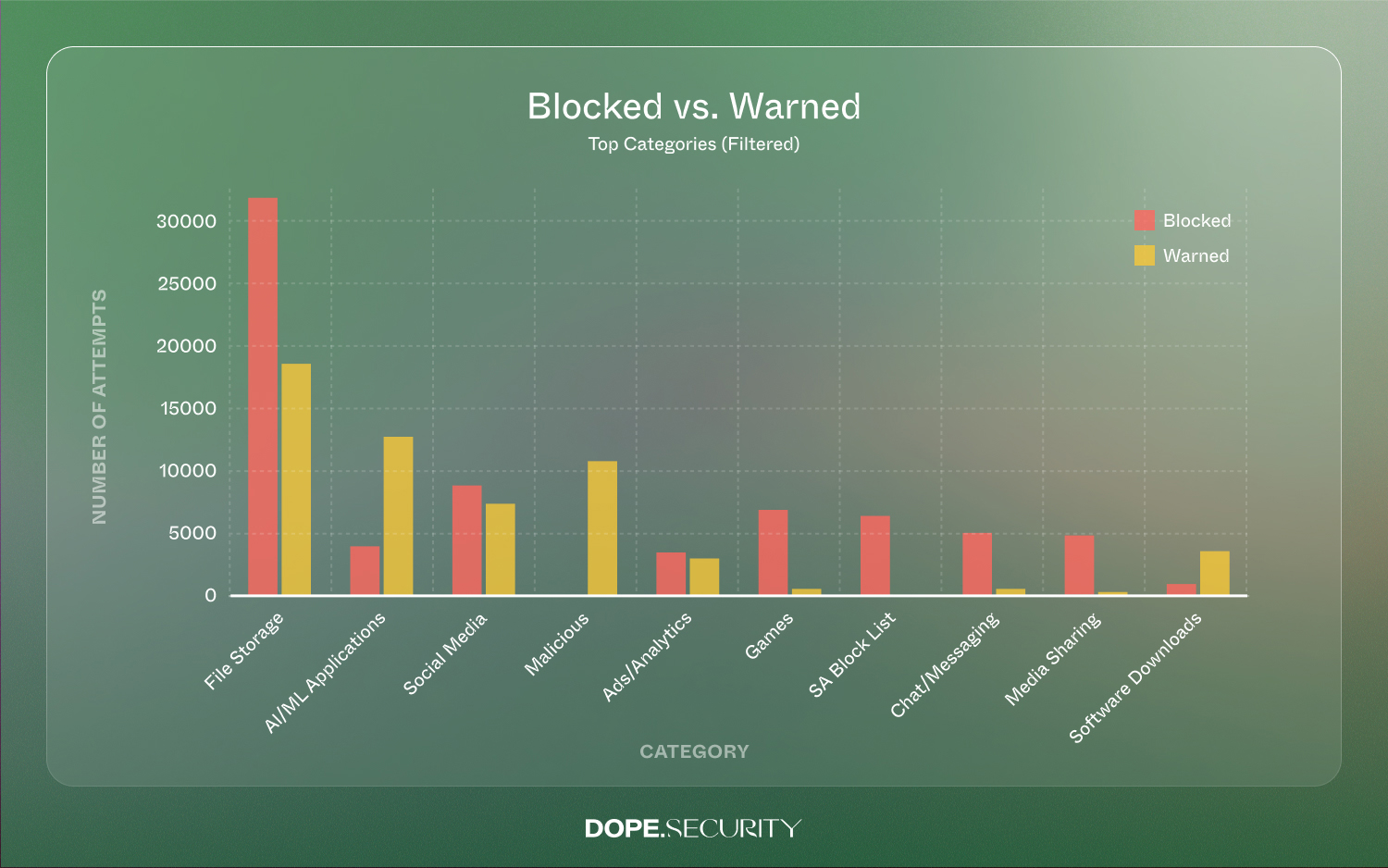
6. Domain Leaderboard: Where Risk and Productivity Collide
Seeing both Microsoft and OpenAI domains pop in the top ranks underscores that “approved” vendors still carry leakage risk when used outside company governance guidelines, including trying to access these domains with personal accounts.
What This Means for CISOs
- Inspect uploads, not just destinations: Cloud drives are here to stay—we can tell by the access requests. dope.security’s AI-powered CASB DLP allows admins to inspect files for sensitive content quickly and accurately, so you know what is being uploaded to which cloud drives.
- Adopt an “educate first” AI strategy: Start with warn-first policies for Gen-AI tools to learn usage patterns and educate users on the company AI policy. Implement stricter controls where needed after your baseline behaviors are understood.
- Bring enforcement on device: A cloud proxy alternative that lives at the endpoint scales instantly with demand and keeps protection active even when the user is offline or other network issues.
If you’re weighing an upgrade from data-center proxies, consider dope.security’s endpoint-based secure web gateway with integrated on-device SWG controls and AI-powered CASB DLP. Book a 30-minute demo; we’ll show how real-time data and local decision-making tighten security without slowing anyone down.












